SSL Pulse: 49% vulnerable to CVE-2014-0224, 14% exploitable
Last week (on June 5th), OpenSSL published an advisory detailing a number of serious problems. The CVE-2014-0224 vulnerability will be the most problematic for most deployments because it can be exploited via an active network (man in the middle) attack.
This vulnerability allows an active network attacker to inject ChangeCipherSpec (CCS) messages to both sides of a connection and force them to fix their keys before all key material is available. Weak keys are negotiated as a result. If you're interested in the details, Adam Langley published a good technical analysis.
Although virtually all versions of OpenSSL are vulnerable, this problem is exploitable only if (1) both sides use OpenSSL and (2) the server uses a vulnerable version of OpenSSL from the 1.0.1 branch.
The good news is that most browsers don't rely on OpenSSL, which means that most browser users won't be affected. However, Android browsers do use OpenSSL and are vulnerable to this attack. Additionally, many command-line and similar programmatic tools use OpenSSL. A particularly interesting target will be various VPN products, provided they are based on OpenSSL (like, for example, OpenVPN).
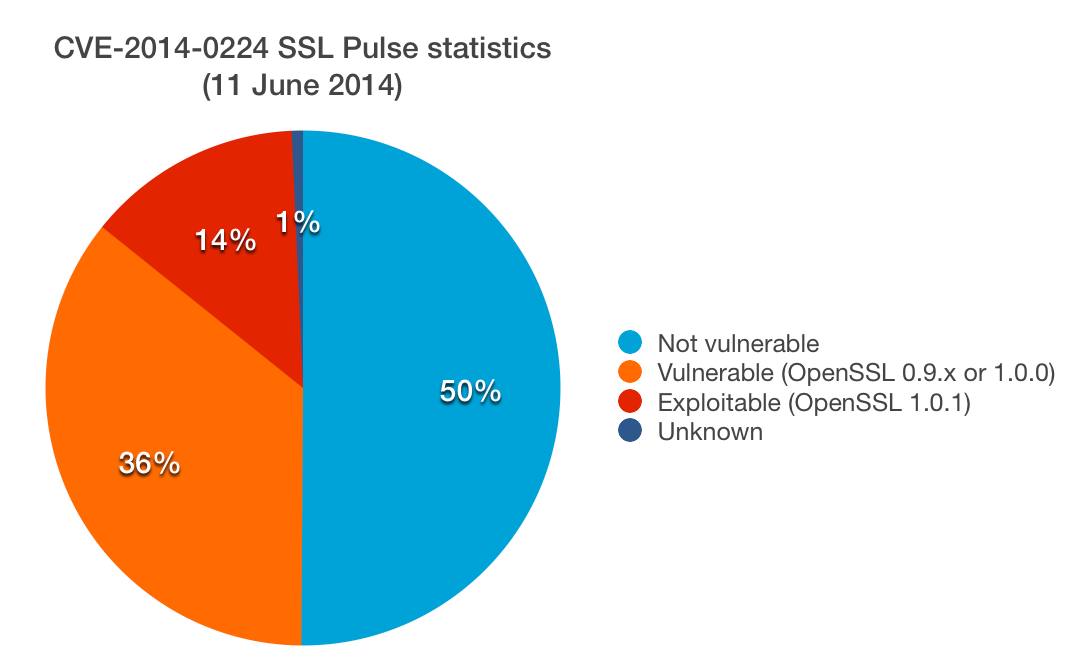
Over at SSL Labs, we've been testing a remote check for CVE-2014-0224 since Friday. Satisfied that the test is identifying vulnerable hosts correctly, yesterday we ran a scan against the SSL Pulse dataset. The results are that about 49% servers are vulnerable. About 14% (of the total number) are exploitable because they're running a newer version of OpenSSL. The rest are probably not exploitable, but should be upgraded because it's possible that there are other ways to exploit this problem.
If you'd like to test your servers, the latest version of SSL Labs incorporates a check for CVE-2014-0224.
 |
MY BOOK: If you like this blog post, you will love Bulletproof TLS and PKI. For system administrators, developers, and IT security professionals, this book provides a comprehensive coverage of the ever-changing field of SSL/TLS and Internet PKI and will teach you everything you need to know to protect your systems from eavesdropping and impersonation attacks. It's available now. |


